Overview
This guide walks you through configuring Okta as your identity provider for Bifrost Enterprise. After completing this setup, your users will be able to sign in to Bifrost using their Okta credentials, with roles and team memberships automatically synchronized.
Prerequisites
- An Okta organization with admin access
- Bifrost Enterprise deployed and accessible
- The redirect URI for your Bifrost instance (e.g.,
https://your-bifrost-domain.com/login)
Step 1: Create an OIDC Application
- Log in to the Okta Admin Console
- Navigate to Applications → Applications
- Click Create App Integration
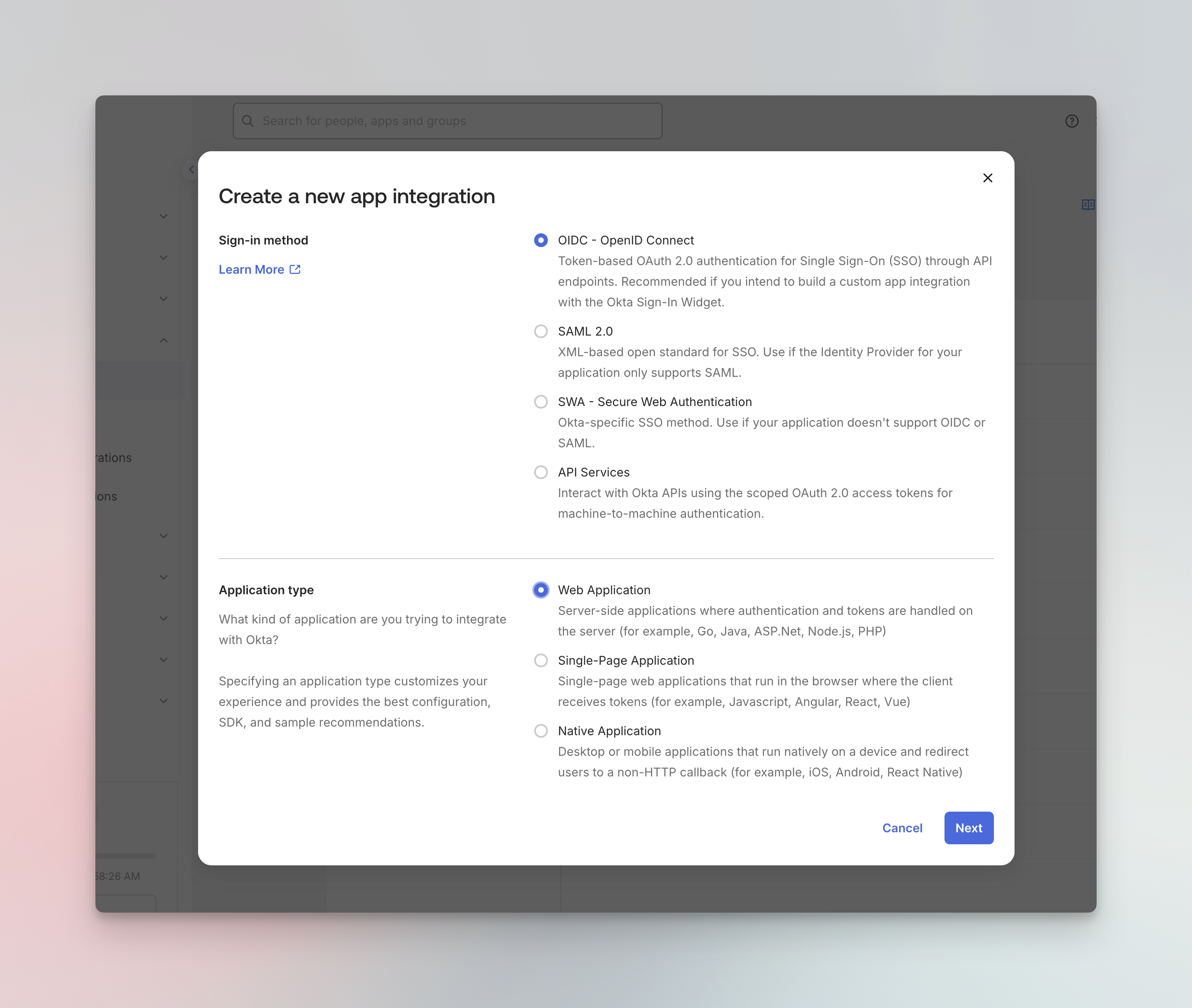
- In the dialog, select:
- Sign-in method: OIDC - OpenID Connect
- Application type: Web Application
- Click Next to continue
Configure the following settings for your application:
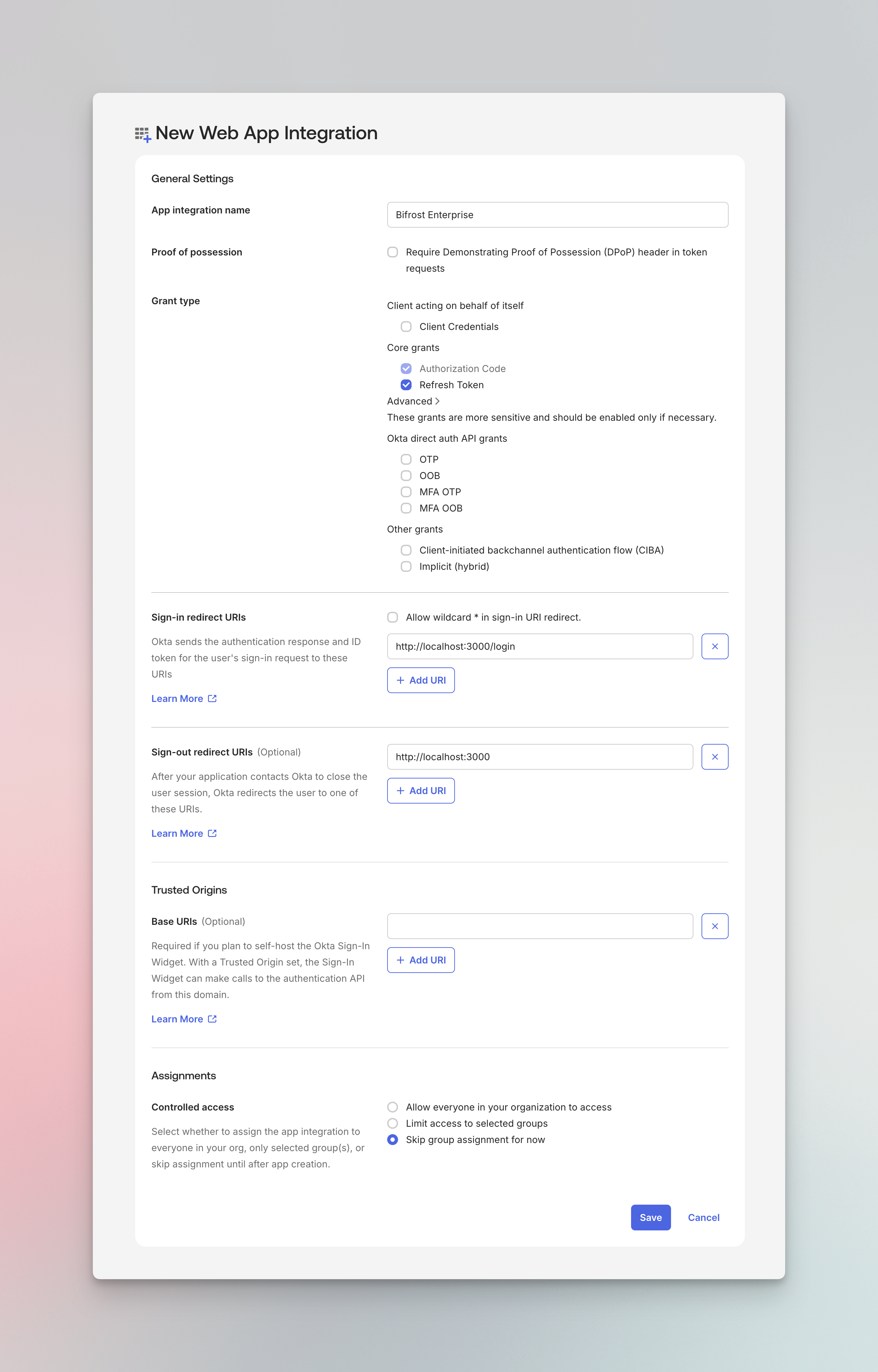
General Settings:
Grant type:
- Enable Authorization Code
- Enable Refresh Token
Sign-in redirect URIs:
- Add your Bifrost login callback URL:
https://your-bifrost-domain.com/login
Sign-out redirect URIs (Optional):
- Add your Bifrost base URL:
https://your-bifrost-domain.com
Assignments:
- Choose Skip group assignment for now (we’ll configure this later)
-
Click Save to create the application
-
After saving, note down the following from the General tab:
- Client ID
- Client Secret (click to reveal)
Bifrost uses Okta’s Authorization Server to issue tokens. You can use the default authorization server or create a custom one.
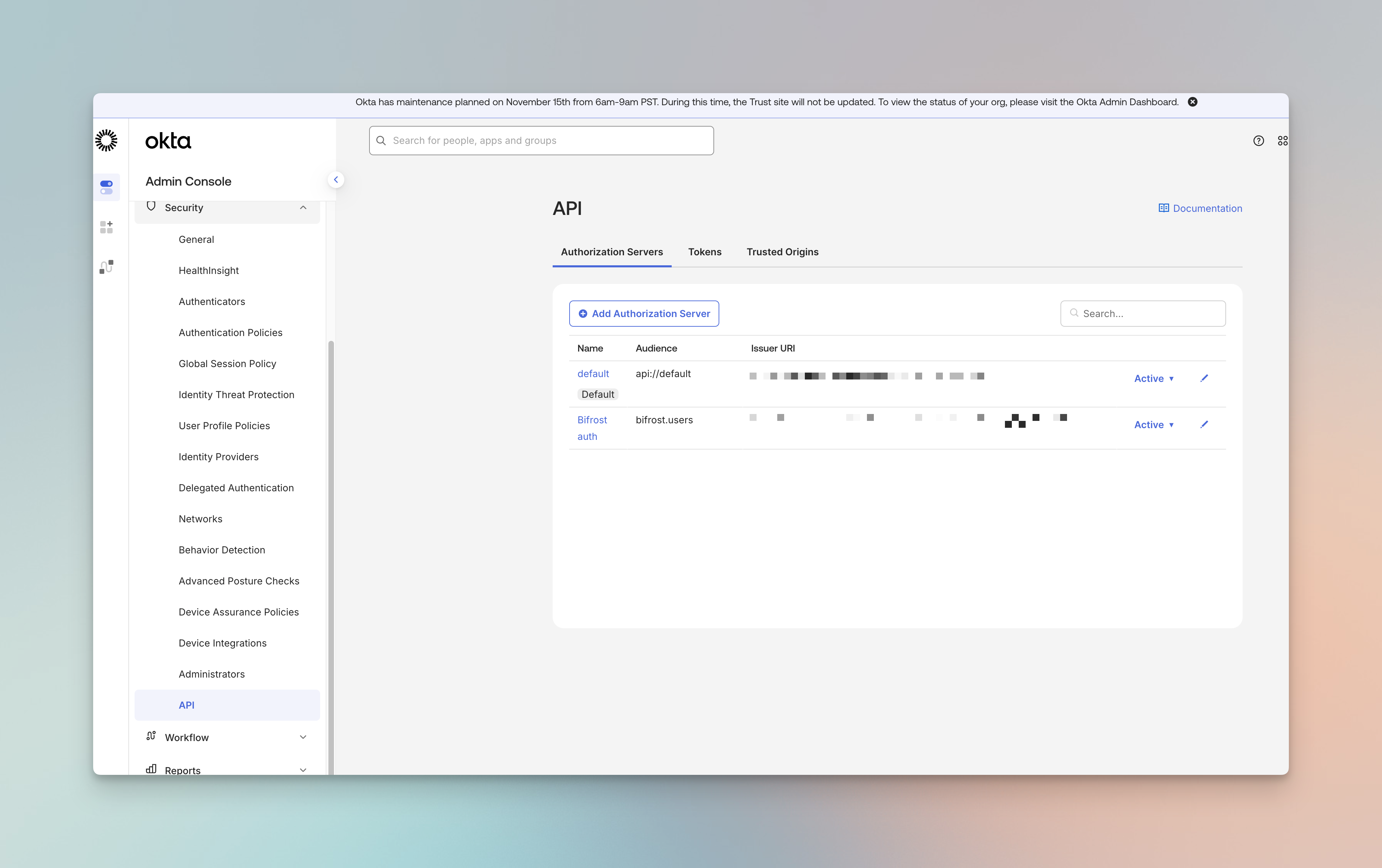
- Navigate to Security → API
- Click on Authorization Servers
- Note the Issuer URI for your authorization server (e.g.,
https://your-domain.okta.com/oauth2/default)
The Issuer URI is used as the issuerUrl in your Bifrost configuration. Make sure to use the full URL including /oauth2/default (or your custom authorization server path).
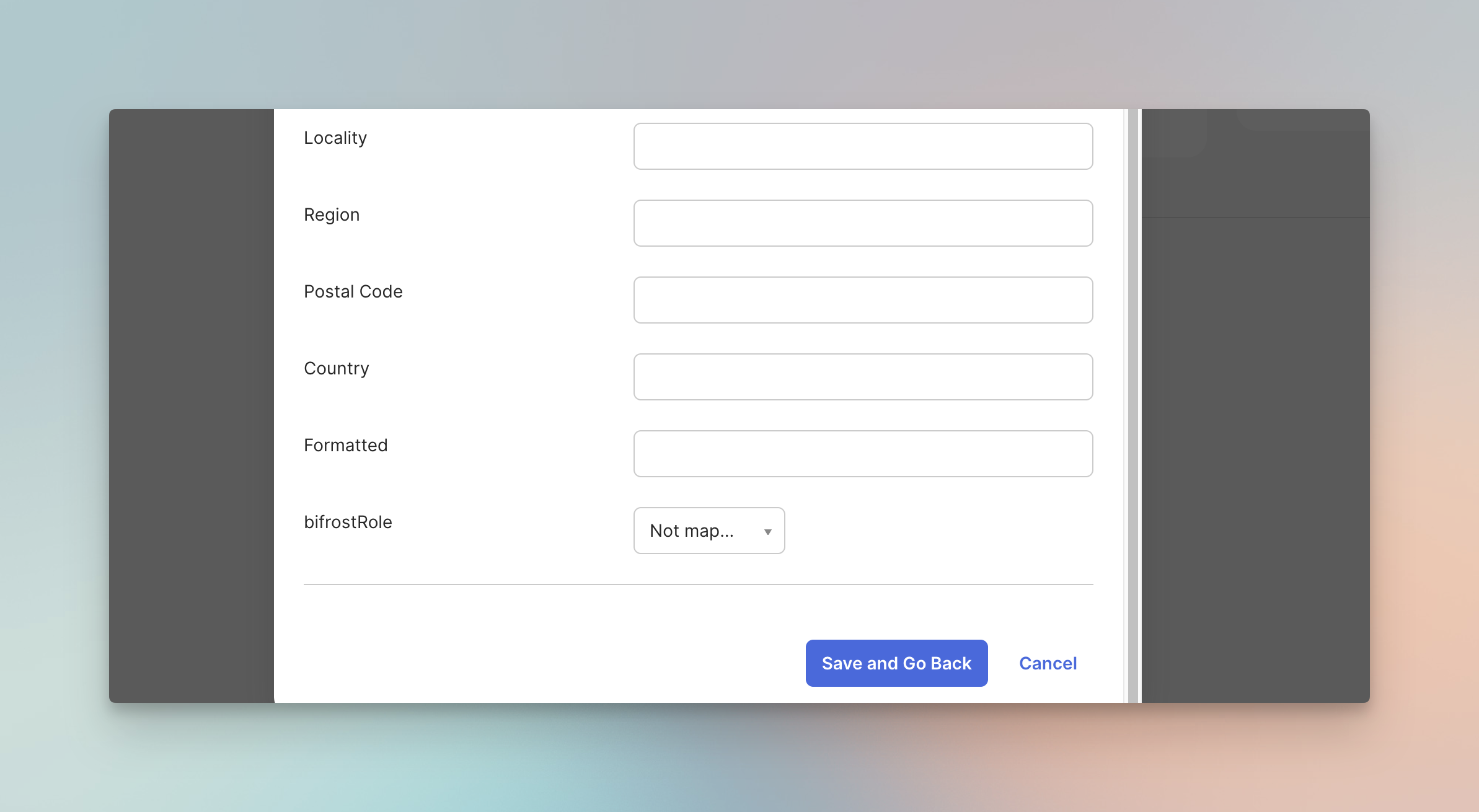
Step 4: Create Custom Role Attribute
To map Okta users to Bifrost roles (Admin, Developer, Viewer), you need to create a custom attribute.
- Navigate to Directory → Profile Editor
- Click on your application’s user profile (e.g., Bifrost Enterprise User)
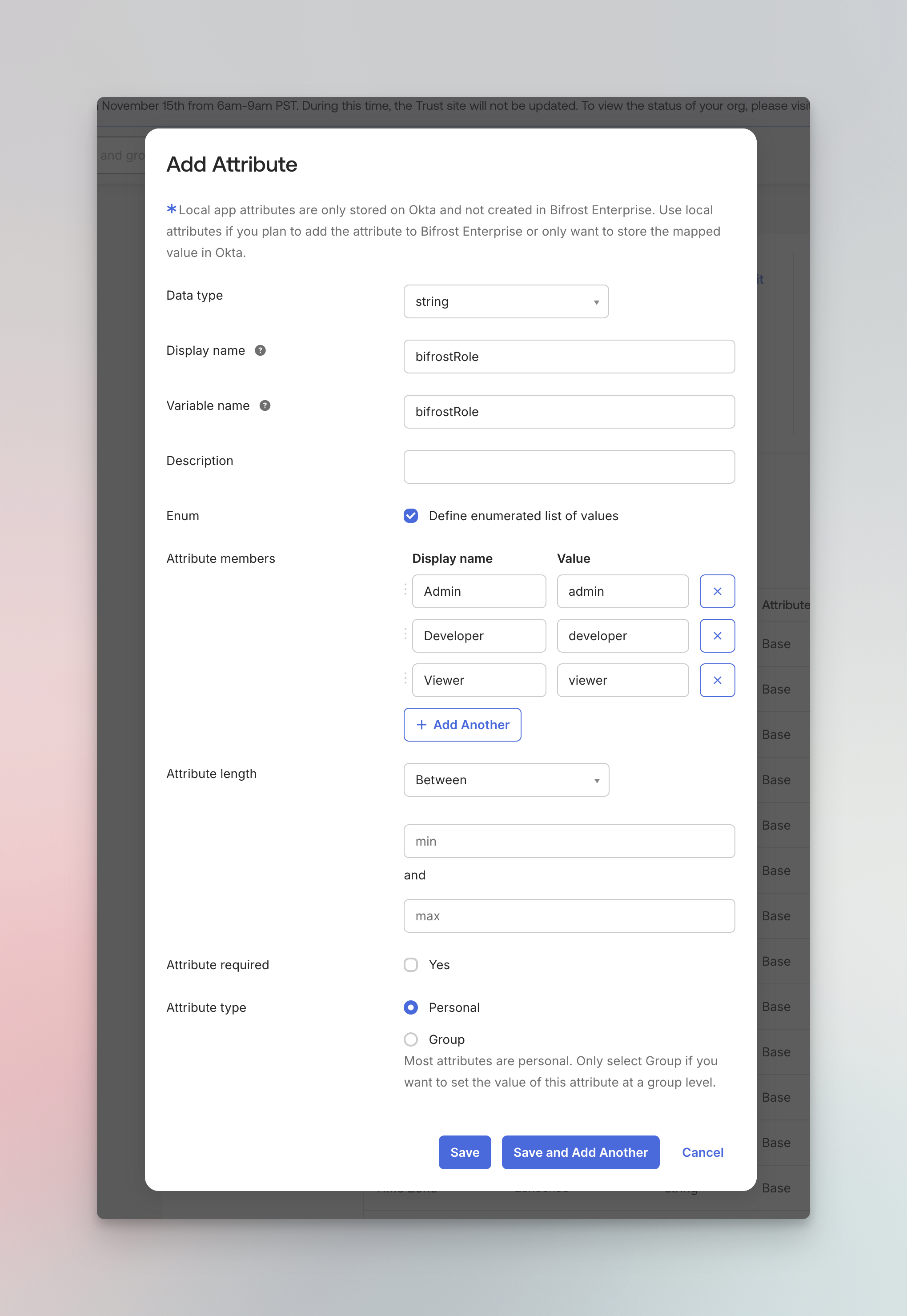
- Click Add Attribute
- Configure the attribute:
| Field | Value |
|---|
| Data type | string |
| Display name | bifrostRole |
| Variable name | bifrostRole |
| Enum | Check “Define enumerated list of values” |
| Attribute members | Admin → admin, Developer → developer, Viewer → viewer |
| Attribute type | Personal |
- Click Save
Step 5: Add Role Claim to Tokens
Configure the authorization server to include the role in the access token.
- Navigate to Security → API → Authorization Servers
- Click on your authorization server (e.g., default)
- Go to the Claims tab
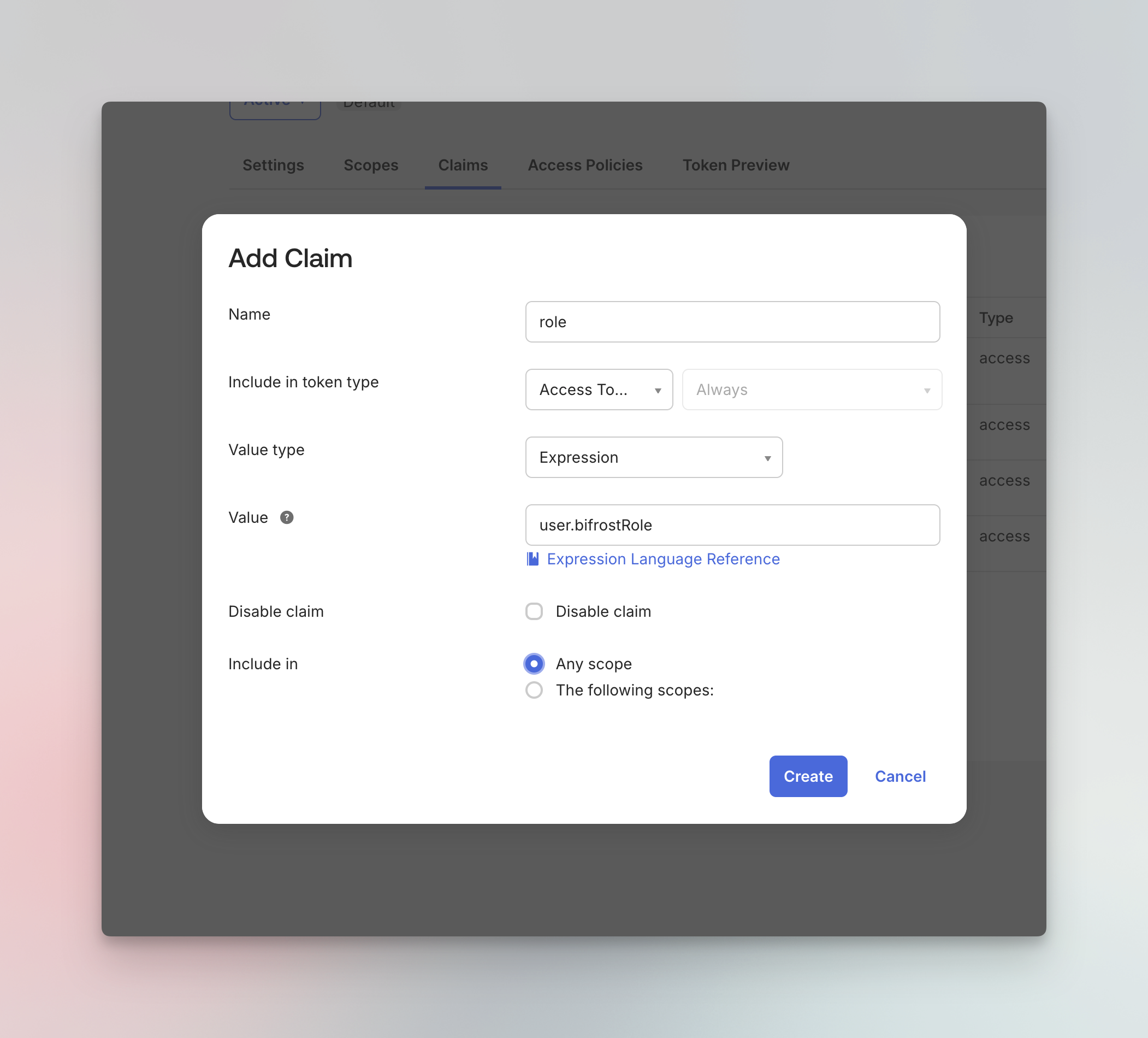
- Click Add Claim
Configure the claim:
| Field | Value |
|---|
| Name | role |
| Include in token type | Access Token, Always |
| Value type | Expression |
| Value | user.bifrostRole |
| Include in | Any scope |
- Click Create
If you named your custom attribute differently, update the Value expression accordingly (e.g., user.yourAttributeName).
Bifrost can automatically sync Okta groups as teams. Users assigned to groups will have their team memberships updated automatically.
Create Groups
- Navigate to Directory → Groups
- Click Add group
- Create groups that correspond to your teams (e.g.,
bifrost-admin, bifrost-developer, ENG, AI)
Add Groups Claim to Tokens
- Go back to Security → API → Authorization Servers
- Select your authorization server
- Go to the Claims tab
- Click Add Claim
Configure the groups claim:
| Field | Value |
|---|
| Name | groups |
| Include in token type | ID Token, Always |
| Value type | Groups |
| Filter | Matches regex: .* (or specify a prefix like bifrost-*) |
| Include in | Any scope |
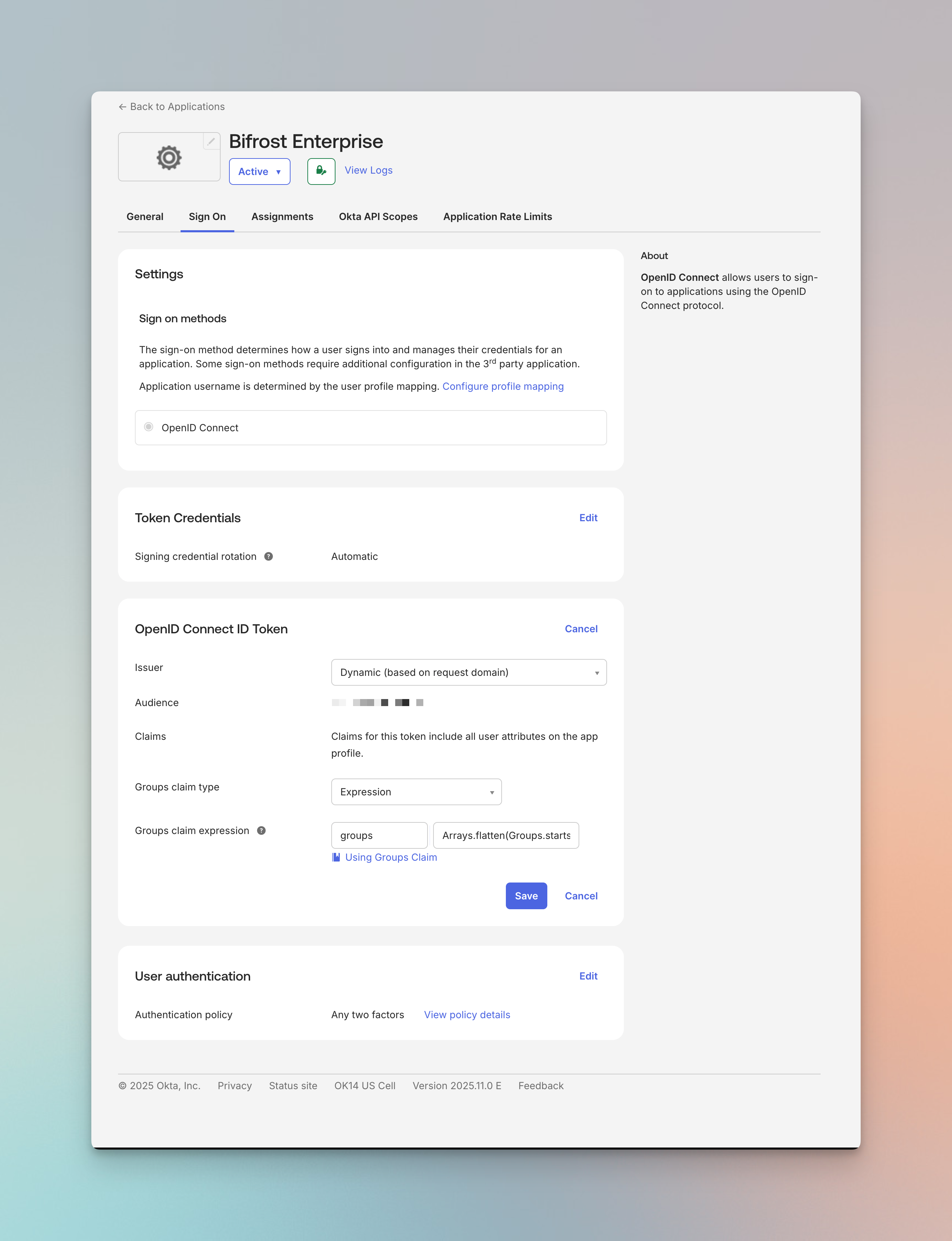
- Navigate to your application’s Sign On tab
- Under OpenID Connect ID Token, configure:
- Groups claim type: Expression
- Groups claim expression:
Arrays.flatten(Groups.startsWith("OKTA", "bifrost", 100))
Adjust the group filter expression based on your naming convention. The example above includes groups starting with “bifrost”.
Step 7: Assign Users to the Application
- Navigate to your application’s Assignments tab
-
Click Assign → Assign to People or Assign to Groups
-
For each user, set their bifrostRole:
- Click Save and Go Back
Now configure Bifrost to use Okta as the identity provider.
Using the Bifrost UI
- Navigate to Workspace → SCIM in your Bifrost dashboard
- Select Okta as the SCIM Provider
- Enter the following configuration:
| Field | Value |
|---|
| Client ID | Your Okta application Client ID |
| Issuer URL | https://your-domain.okta.com/oauth2/default |
| Audience | Your API audience (e.g., api://default or custom) |
| Client Secret | Your Okta application Client Secret (optional, for token revocation) |
- Toggle Enabled to activate the provider
- Click Save Configuration
After saving, you’ll need to restart your Bifrost server for the changes to take effect.
Configuration Reference
| Field | Required | Description |
|---|
issuerUrl | Yes | Okta authorization server URL (e.g., https://your-domain.okta.com/oauth2/default) |
clientId | Yes | Application Client ID from Okta |
clientSecret | No | Application Client Secret (enables token revocation) |
audience | Yes | API audience identifier from your authorization server |
userIdField | No | JWT claim for user ID (default: uid) |
rolesField | No | JWT claim for roles (default: roles) |
teamIdsField | No | JWT claim for group/team IDs (default: groups) |
Testing the Integration
- Open your Bifrost dashboard in a new browser or incognito window
- You should be redirected to Okta for authentication
- Log in with an assigned user
- After successful authentication, you’ll be redirected back to Bifrost
- Verify the user appears in the Bifrost users list with the correct role
Troubleshooting
User not redirected to Okta
- Verify the SCIM provider is enabled in Bifrost
- Check that the Bifrost server was restarted after configuration
- Ensure the Issuer URL is correct and accessible
”Invalid audience” error
- Verify the
audience field matches your Okta authorization server’s audience
- Check if you’re using a custom authorization server and update the issuer URL accordingly
Roles not syncing
- Ensure the
role claim is configured in your authorization server
- Verify users have the
bifrostRole attribute set
- Check that the claim is included in the access token (use Okta’s Token Preview feature)
Groups not appearing as teams
- Verify the
groups claim is configured in your authorization server
- Ensure users are assigned to the relevant groups
- Check that groups are assigned to the application
Token refresh failing
- Ensure the Refresh Token grant type is enabled for your application
- Verify the
offline_access scope is included in your authorization requests
Next Steps