Overview
Virtual Keys are the primary governance entity in Bifrost. Users and applications authenticate using the given headers to access virtual keys and get specific access permissions, budgets, and rate limits. Allowed Headers:x-bf-vk- Virtual key header, eg.sk-bf-*Authorization- Authorization header, eg.Bearer sk-bf-*(OpenAI style)x-api-key- API key header, eg.sk-bf-*(Anthropic style)x-goog-api-key- API key header, eg.sk-bf-*(Google Gemini style)
Old virtual keys(without
sk-bf-* prefix) are only supported by x-bf-vk header.You can also use
Authorization, x-api-key and x-goog-api-key headers to pass direct keys to the provider. Read more about it in Direct Key Bypass.- Access Control - Model and provider filtering
- Cost Management - Independent budgets (checked along with team/customer budgets if attached)
- Rate Limiting - Token and request-based throttling (VK-level only)
- Key Restrictions - Limit VK to specific provider API keys (if configured, VK can only use those keys)
- Exclusive Attachment - Belongs to either one team OR one customer OR neither (mutually exclusive)
- Active/Inactive Status - Enable/disable access instantly
Configuration
- Web UI
- API
- config.json
- Go to Virtual Keys
-
Click on Add Virtual Key button
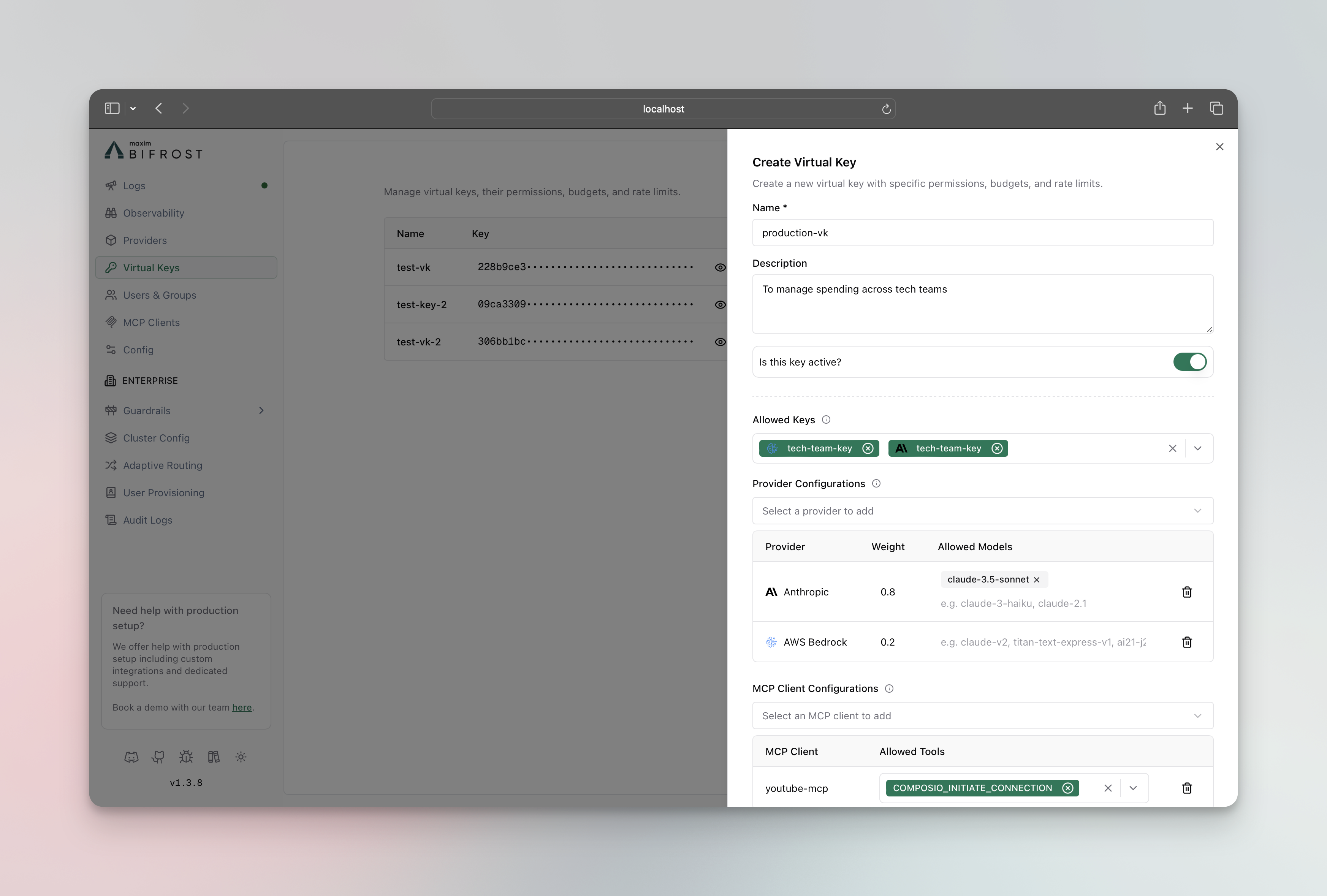
- Max Limit: Dollar amount (e.g.,
10.50) - Reset Duration:
1m,1h,1d,1w,1M
- Token Limit: Max tokens per period
- Request Limit: Max requests per period
- Reset Duration: Reset frequency for each limit
- Team: Assign to existing team (mutually exclusive with customer)
- Customer: Assign to existing customer (mutually exclusive with team)
- Click Create Virtual Key
User Groups
Teams
Teams provide organizational grouping for virtual keys with department-level budget management. Teams can belong to one customer and have their own independent budget allocation. Key Features:- Organizational Structure - Group multiple virtual keys
- Independent Budgets - Department-level cost control (separate from customer budgets)
- Customer Association - Can belong to one customer (optional)
- No Rate Limits - Teams cannot have rate limits (VK-level only)
- Web UI
- API
- config.json
- Go to Users & Groups → Teams
-
Click on Add Team button
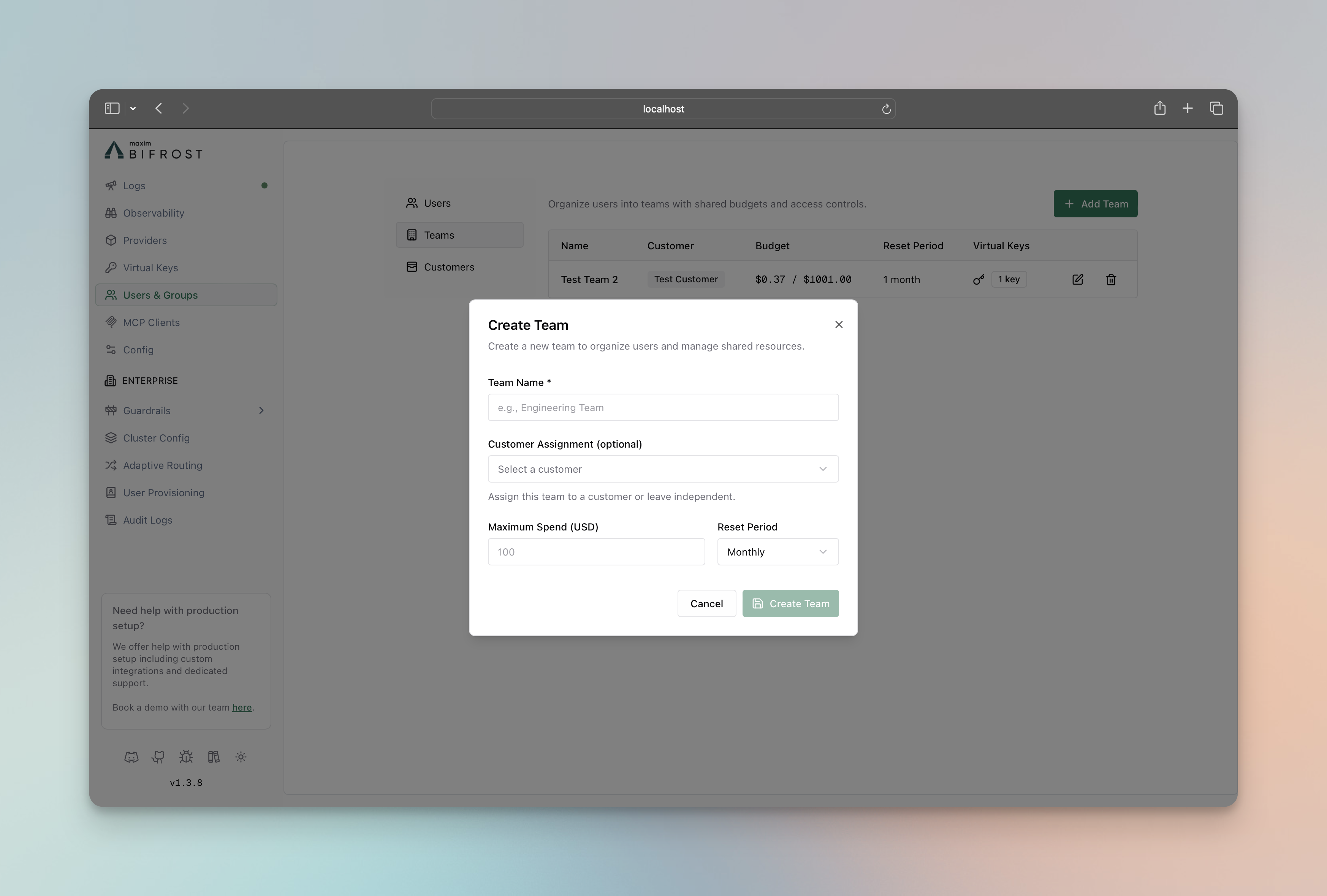
- Assign Virtual Keys to Team
- Go to Virtual Keys page
- Edit the virtual key and assign it to the team
- Click on Save button
Customers
Customers represent the highest level in the governance hierarchy, typically corresponding to organizations or major business units. They provide top-level budget control and organizational structure. Key Features:- Top-Level Organization - Highest hierarchy level
- Independent Budgets - Organization-wide cost control (separate from team/VK budgets)
- Team Management - Contains multiple teams and direct VKs
- No Rate Limits - Customers cannot have rate limits (VK-level only)
- Web UI
- API
- config.json
- Go to Users & Groups → Customers
-
Click on Add Customer button
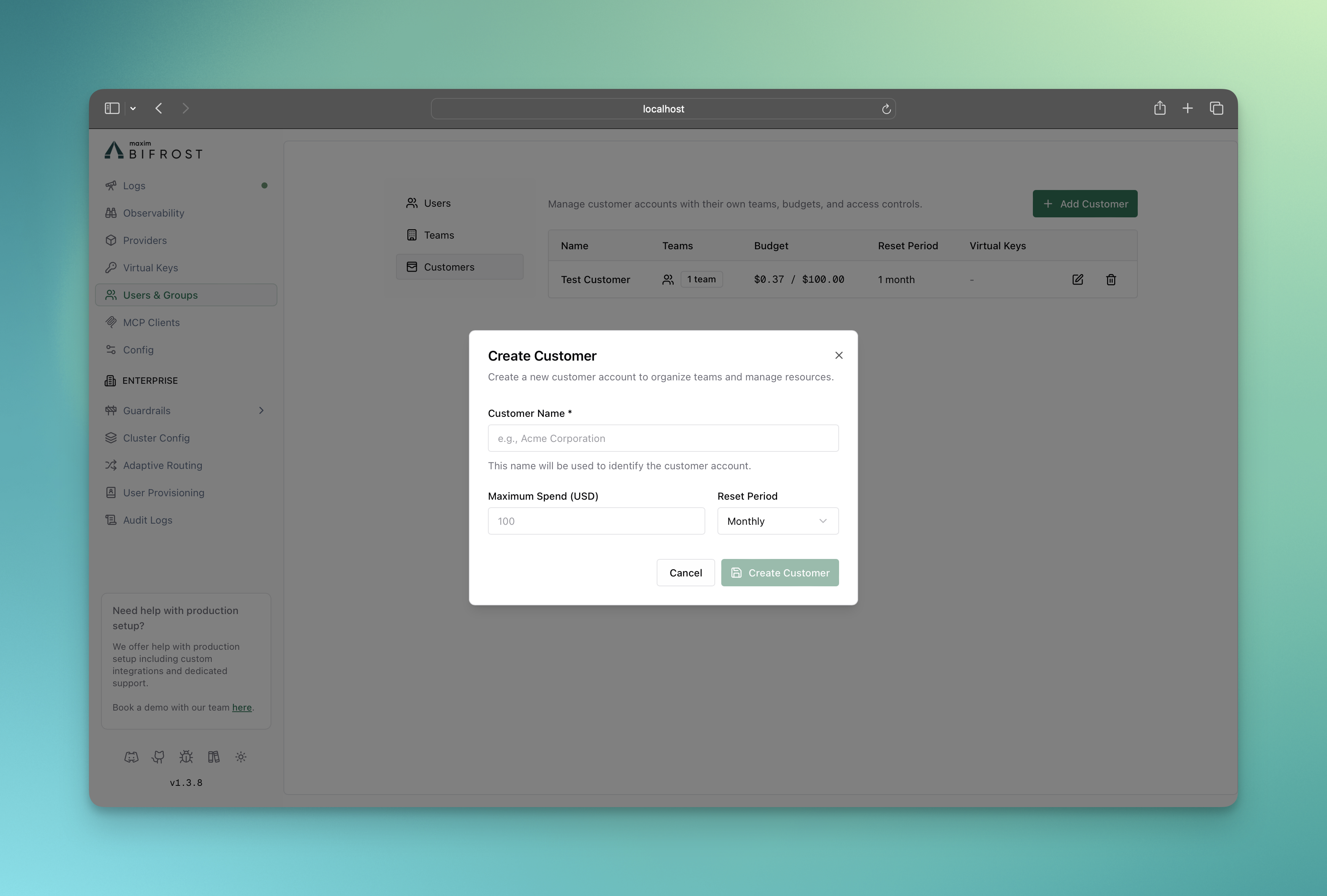
-
Assign Teams to Customer
- Go to Teams page
- Edit the team and assign it to the customer
- Click on Save button
-
Assign Virtual Keys to Customer
- Go to Virtual Keys page
- Edit the virtual key and assign it to the customer
- Click on Save button
Features
- Budget and Limits - Enterprise-grade budget management and cost control and rate limiting using virtual keys
- Routing - Route requests to the appropriate providers/models and restrict api keys using virtual keys
- MCP Tool Filtering - Manage MCP clients/tools for virtual keys
Usage
Required Header
All governance-enabled requests must include the virtual key header:x-bf-vk header is not present, the request will be allowed but without any governance checks/routing. But you can make it mandatory by enforcing the governance header.
- Web UI
- API
- config.json
- Go to Client → Governance
- Check the Enforce Governance Header checkbox
x-bf-vk header is not present.
Optional Audit Headers
Include additional headers for enhanced tracking and audit trails:x-bf-vk- Required virtual key for access control
Error Responses
- Virtual Key Not Found (400)
- Virtual Key Blocked (403)
- Rate Limit Exceeded (429)
- Token Limit Exceeded (429)
- Request Limit Exceeded (429)
- Budget Exceeded (402)
- Model Not Allowed (403)
- Provider Not Allowed (403)

